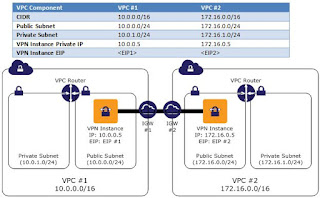
Today i will show how to setup a complete VPC(Virtual Private Cloud) between 2 Data Centers in different Regions(I will use AWS Oregon and AWS N California) this is mandatory to test and run multi-data center solutions, we will need create a VPN(Virtual Private Network) over the internet, todo such a task we will use Open Swan.
This task is very complicated and have several steps its easy to make some mistake and mess with everything so be very careful, the whole exercise could easily take 3h or more. Also want say thanks to my Friend Joao Palma(AWS Solution Architect)who supported me on this task :-) and have extreme patience and know-how on the hard-core devops amazon cloud things :-)
Screen Shots
0_oregon_vpc
1_vpc_california
2_create_sg_nat
3_sg_nat_acess_himself
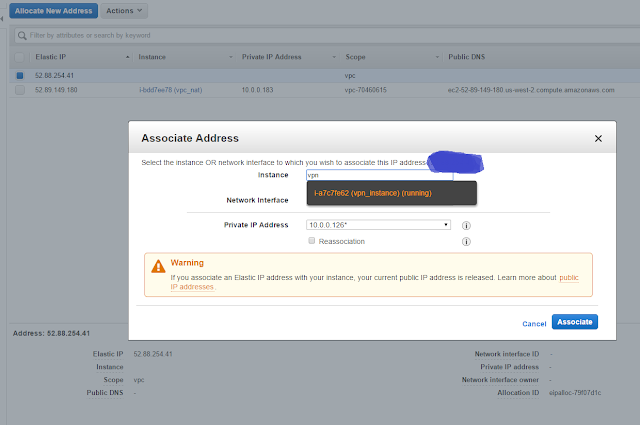
4_eip_vpn_nat_california
5_eip_vpn_nat_oregon
6_disable_source_check
7_vpn_instance_nat_california
8_vpn_instance_oregon
9_sg_vpn_instance_oregon
10_sg_vpn_instance_caliornia
11_ENI_california
12_eni_oregon
14_route_table_california
14_route_table_oregon
Cheers,
Diego Pacheco
This task is very complicated and have several steps its easy to make some mistake and mess with everything so be very careful, the whole exercise could easily take 3h or more. Also want say thanks to my Friend Joao Palma(AWS Solution Architect)who supported me on this task :-) and have extreme patience and know-how on the hard-core devops amazon cloud things :-)
Screen Shots
0_oregon_vpc
1_vpc_california
2_create_sg_nat
3_sg_nat_acess_himself
4_eip_vpn_nat_california
5_eip_vpn_nat_oregon
6_disable_source_check
7_vpn_instance_nat_california
8_vpn_instance_oregon
9_sg_vpn_instance_oregon
10_sg_vpn_instance_caliornia
11_ENI_california
12_eni_oregon
14_route_table_california
14_route_table_oregon
Cheers,
Diego Pacheco






















comment 0 comments